
Please note that this blog is archived and outdated. For the most current information click here!
Safety First: Tackling Security Threats in Cloud Computing
Cloud services have become invaluable for businesses of all sizes with the benefits they present. Decreased infrastructure costs, continuous
delivery, access to wider markets and better interaction with mobile apps are all advantages of cloud computing. So why is it that some
companies remain sceptical about moving to the cloud?
74% of IT executives and CIO's cited cloud computing security as the top challenge preventing their adoption of the cloud services
model. There's been this negative publicity surrounding the cloud following some serious data leaks by major corporate entities. I'm sure
you've heard about Equifax, one of the largest credit bureaus in the US, that had a data breach leaking personal information of over 14.9
million consumers. This prompted widespread criticism and a general belief that moving to the cloud is unsafe. However for the most part,
these security concerns are preventable.
Software as a Service is a form of cloud computing where applications are hosted by the service provider and made available to clients over
the internet. In SaaS, the client has to depend on the provider for proper security measures. The provider must ensure that multiple users
do not see each other's data. SaaS is concerned with substituting applications, hence providers must ensure they preserve the security
functionality provided by the legacy application in order to achieve a successful data migration. For more on migrating applications
to the cloud.
Data Security
In the SaaS model, the enterprise data is stored outside the enterprise boundary. Because the data is stored at the vendor's end, they must
remain accountable for conducting additional security checks to ensure data security. In order to overcome this vulnerability, vendors use
assessments to test and validate the security of the data. Some assessments include, but are not limited to, cross site scripting, OS and
SQL injection flaws, cross-site request forgery and cookie manipulation. The range of assessments and tests highlight the importance of a
reliable vendor when moving to the cloud.
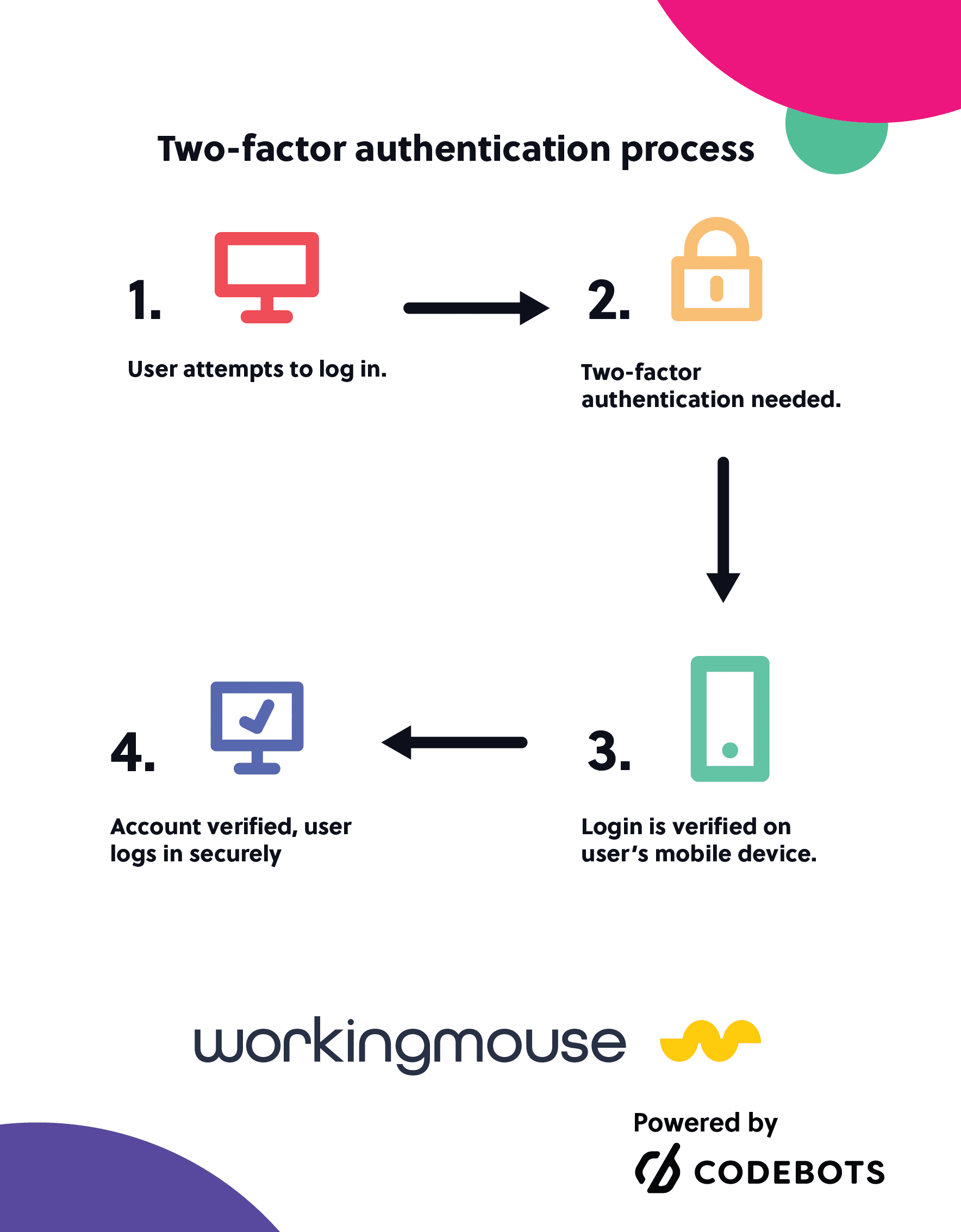
Vendors that offer a high level of security will also offer two-factor authentication tools (2FA) for user logins, to protect users from
data leaks. These 2FAs require a second verification, beyond a password, for a person to login to an account. An example would be a code
sent to your phone, or a thumbprint scan. This type of verification cannot be replicated by someone who obtains data leaked by the cloud.
Data Integrity
Data integrity in a standalone system is achieved via database constraints. Cloud computing somewhat complicates this because there is a mix
of on-premise and SaaS applications exposed as service. HTTP does not support transactions or guaranteed delivery, so the only option is to
implement these at the API level. Vendors must approach this security threat cautiously when moving applications to the cloud.
Data Segregation
Hosting multiple clients data is one of the major traits of cloud computing; hence multiple users can store their data. Intrusion of data of
one user by another becomes possible since the data is hosted in the same location. This intrusion can be done either by hacking through the
loop holes in the application or by injecting client code into the SaaS system. To ensure intrusions are not possible, the system must be
able to segregate the data from different users.
Data Confidentiality
Due to the nature of cloud computing, companies dealing with confidential information will need to disclose that information to the vendor.
This raises confidentiality concerns. A good vendor will offer to sign a non-disclosure agreement to address this issue. This ensures that
any breach caused negligently by them is legally actionable by your company.
I'm not purporting to put anyone off cloud computing, on the contrary, I'm a big fan of cloud computing. This article is simply ensuring you
know about the risks associated with it. Once these risks are addressed, you will enjoy digging up and unleashing your cloud
migration. Don't be that person who parks in 2 hour zone for 4 hours and naively believes they'll be ok. Be cautious and you will be amazed
with the benefits of cloud computing.















.png)

