
Metamodels for ISMS Success
TLDR
Meta Models
- WM uses metamodels for defining relationships, automating documentation and code generation.
- Original ISMS metamodel managed ISO27001, covering various aspects of management.
- New ISMS metamodel has been broken down into adaptable parts, allowing the capability to integrate other standards like ISO 9001
- New ISMS metamodel cross-references common ISO models, and roles, improving risk identification and management.
ISMS Cheat Sheet
- ISMS cheat sheet integrated with Codebots and Gitlab, updating templates to reflect the new modular structure.
- This links individuals to their teams and roles, ensuring accurate task assignments and document references.
- This simplifies extraction of all registered risks and enhances verification processes and system modularity.
Meta Models for ISMS
I recently interviewed Nathan, a senior software developer at WorkingMouse who also serves on our ISMS committee. Nathan has been focusing on updating our original ISMS meta models to include reusable components for future ISMS standards, as well as developing an ISMS cheat sheet. This blog post dives into WorkingMouse’s approach to leveraging metamodels for ISMS management, highlighting our newly integrated ISMS cheat sheet integrated via the Codebots platform and Gitlab.
Information Security Management System (ISMS) is essential for organisations, providing a structured approach to protecting sensitive information. Implementing an ISMS helps organisations safeguard valuable assets, such as customer data, financial records, and intellectual property, from unauthorised access and breaches.
ISMS fosters a proactive approach to identifying and mitigating information security risks, thereby enhancing overall resilience against cyber threats. Additionally, it supports business continuity planning, ensuring that critical operations can continue uninterrupted during disruptions. Moreover, an ISMS plays a crucial role in maintaining stakeholder trust, enhancing operational efficiency, and securing a competitive advantage. To illustrate these benefits, I’ve discussed with Nathan how WorkingMouse coordinates its ISMS using metamodels.
What are Meta Models?
A metamodel describes the data within a model, such as an excel spreadsheet where the column names/types serve as the metamodel and the data in each row represents the model. At WorkingMouse our metamodels consist of classes or types of objects that define things and their relationships. When integrated with Codebots pipelines, this combination allows us to automate the generation of artifacts like documentation and code, eliminating the need for manual writing. Using metamodels is essentially like a schema that define data structures within models. For instance, they capture crucial details about technologies such as their names, versions, and types (e.g., applications, hardware, libraries, or services) in a controlled list, called an Enum.
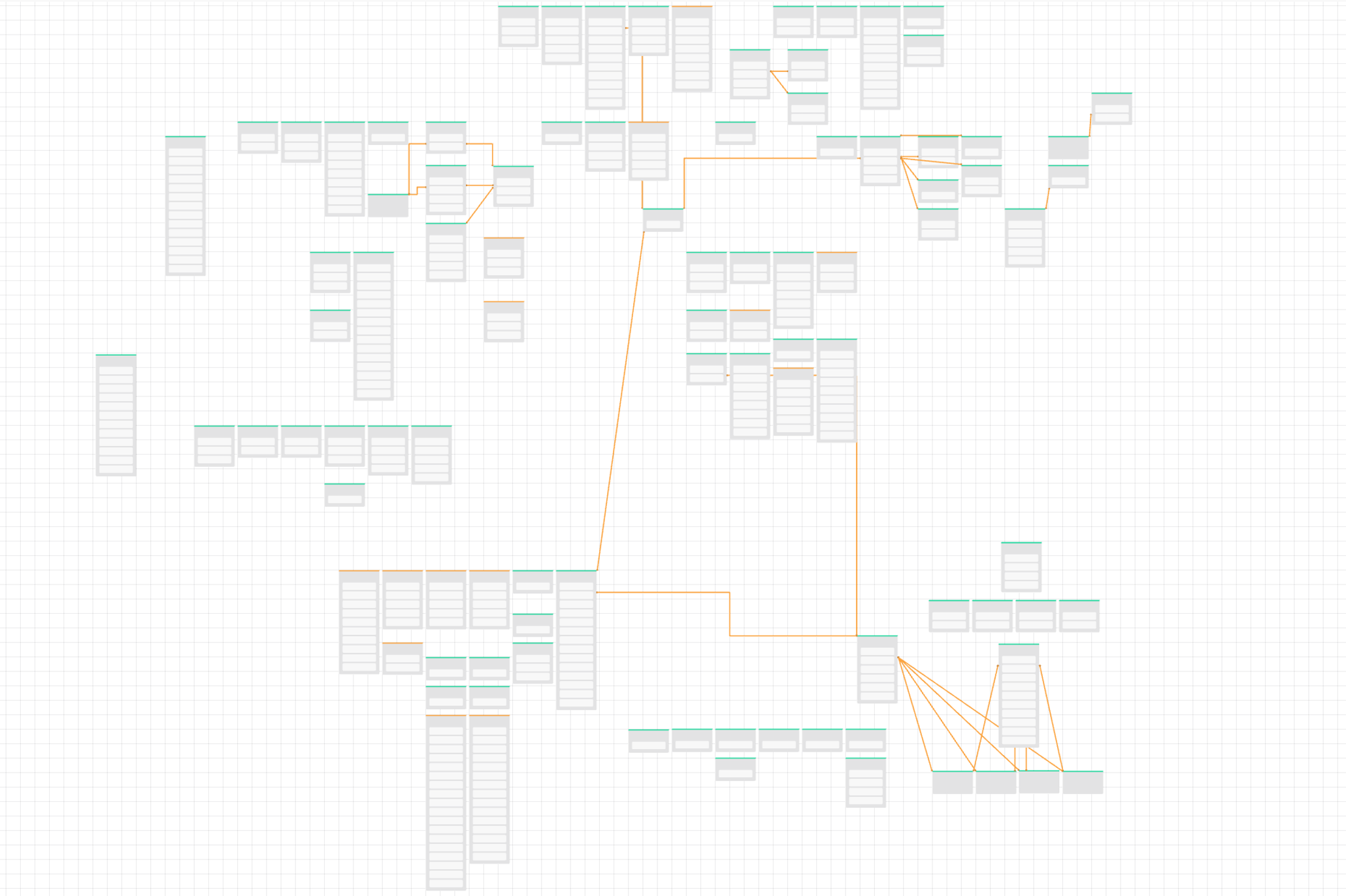
Original ISMS Model
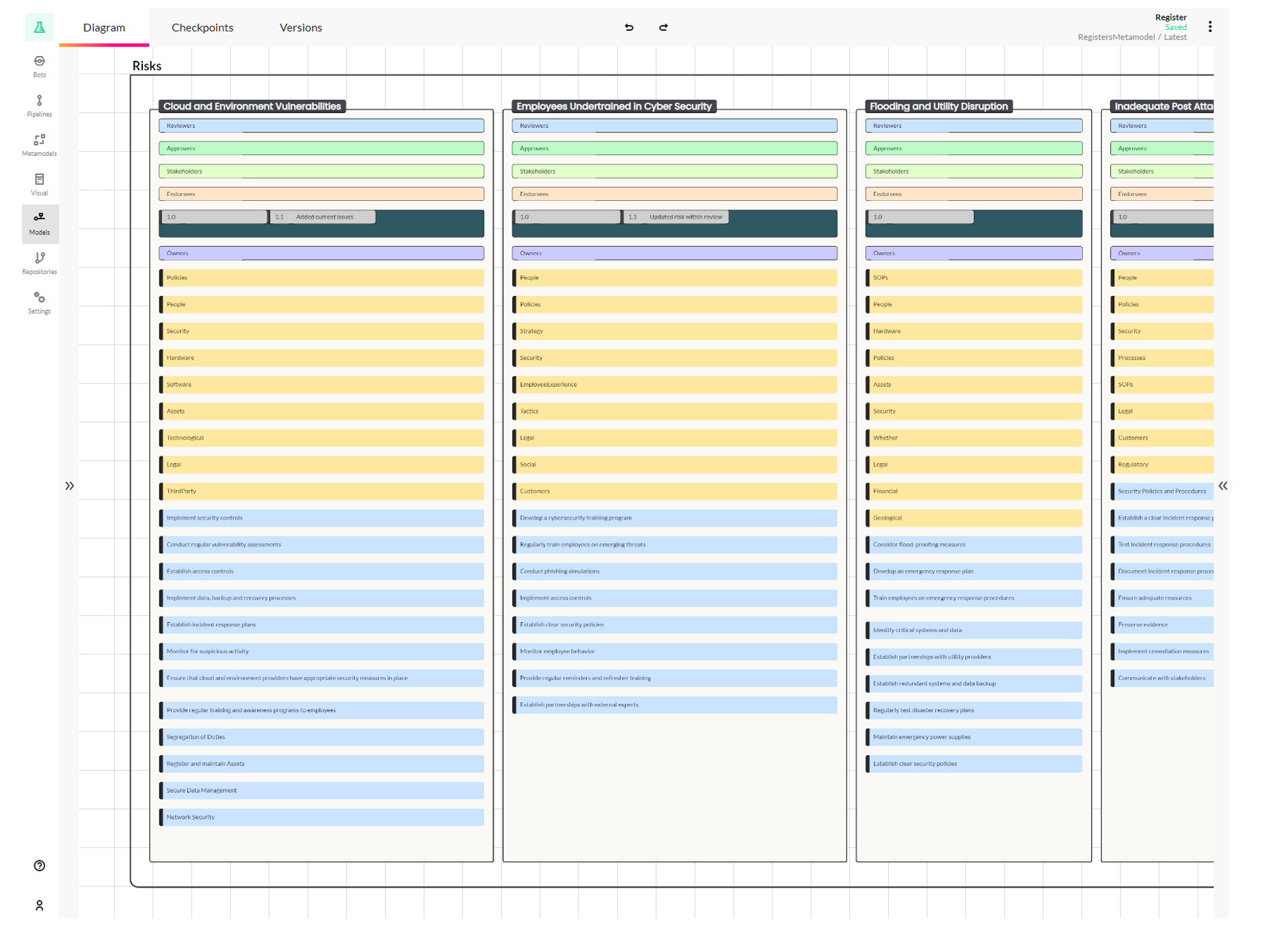
The original ISMS model was built for managing ISO27001 and was quite a large meta model. The model encompassed various aspects related to managing content, the actual clauses in the ISO standard, and how they map to metrics and objectives as part of the ISMS. Nate has been working to break the model up, so that in future, if we want to include more than just the ISMS standard – like the quality standards (ISO 9001) and others, we can have the common elements centralised. Essentially, the goal was to dismantle the old metamodel so that it could be adaptable by other metamodels.
New ISMS Model
To achieve this, the easiest way to proceed is by examining the ISO metamodel. Essentially, this metamodel serves as a scheme for describing the data within the model. For instance, if we want to capture information about technology, we include details such as name, version, and type of technology, which is controlled via an Enum (application, hardware, library, or service).
The idea is that individual classes within a metamodel describe the data that can be included. With the new version of the platform, we can now cross-reference meta models. This means the ISMS metamodel can refer to the common ISO metamodel, which in turn refers to the Roles metamodel, the Teams, and Registers metamodels. The Registers component involves the risks associated with the ISMS, which other standards might also identify. The image below illustrates how everything has been broken up and how the components are segmented, whereas previously, it was one unified system.
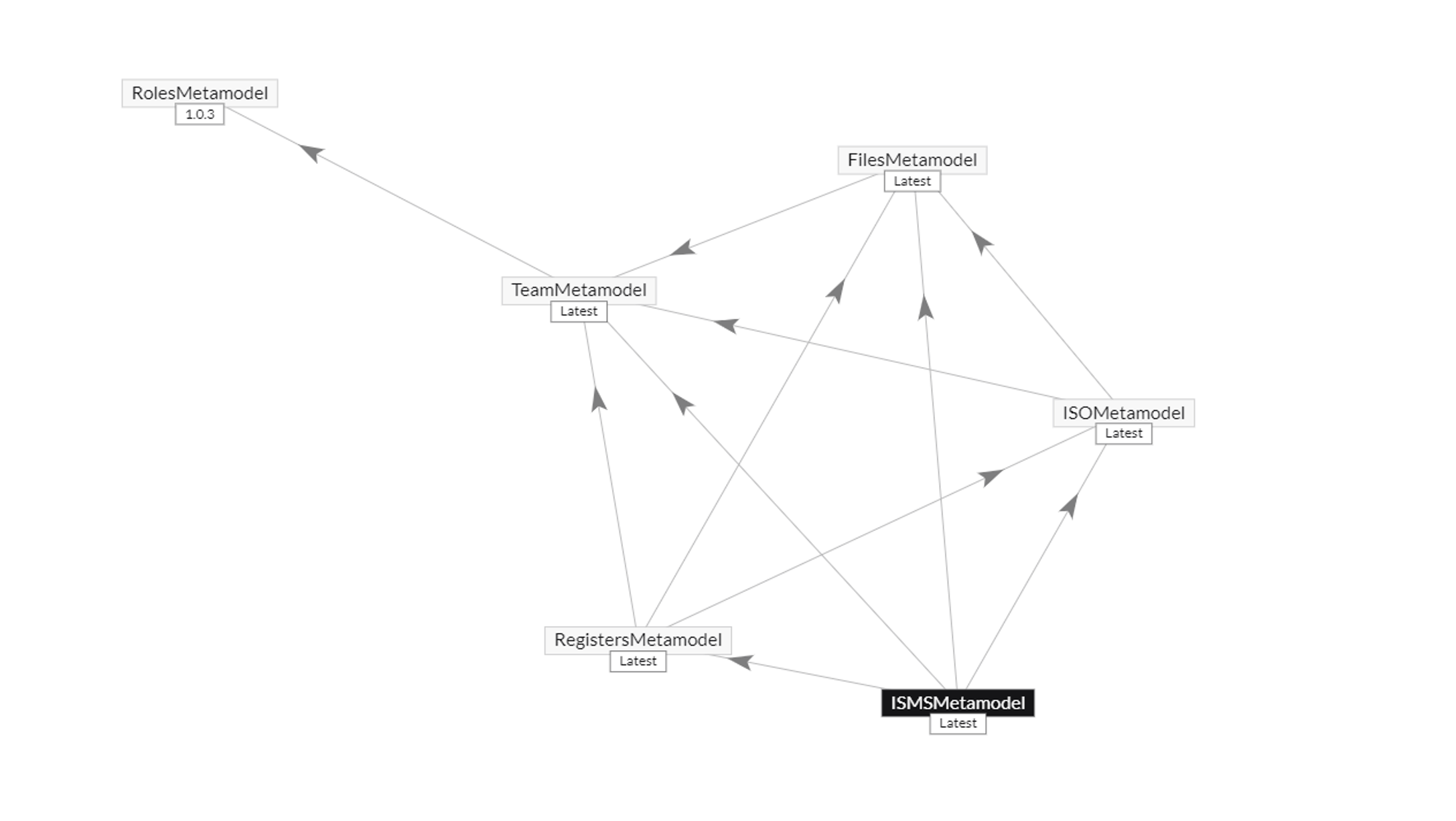
This integration allows for a comprehensive identification of risks associated with the ISMS, distinguishing this structured approach from previous methods where all data was aggregated without differentiation. The register itself highlights the risks associated specifically with the ISMS, while other standards may identify additional risks.
ISMS Cheat Sheet
Building on this structured approach, Nathan has been working on creating an ISMS cheat sheet that is integrated through the Codebots platform and GitLab. Previously, everything was centralised, but now this model references the team whenever a person is mentioned in the files. When we view versions related to the team, we see that the team relies on roles. Whenever a role appears in a diagram against a person, it refers to the roles in this separate model.
In generating content from these models, Nathan has gone through and updated all the templates that referred to parts of the old ISMS. For instance, if the Risk register template previously referenced the original ISMS, it now references the Registers model. This change allows us to extract all the risks registered in the Register model. Additionally, a new feature that Nathan has been working on involves the inclusion of people, this has helped verify that all relationships are correctly re-established.
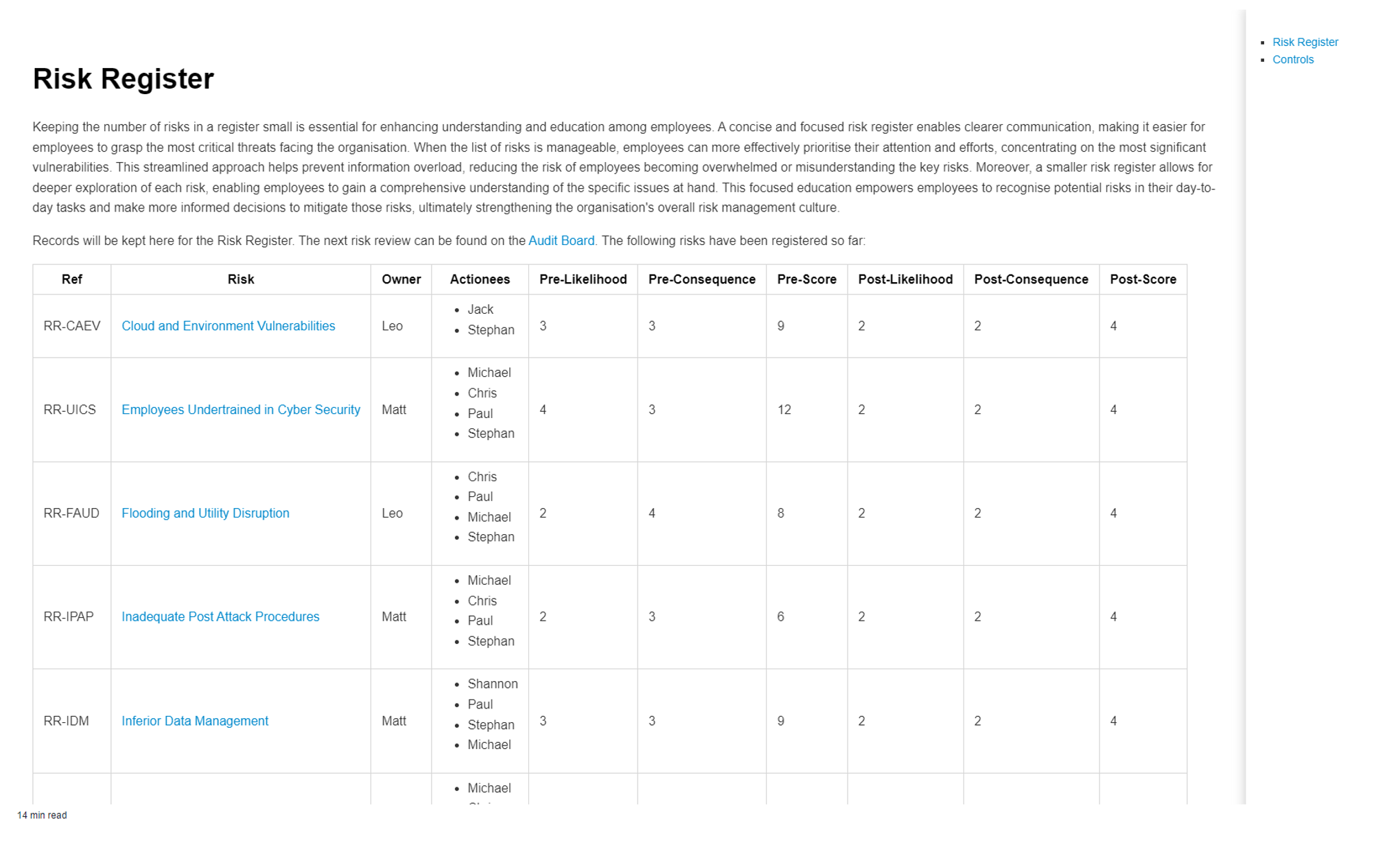
For example, when we load our CSO, Matt, and preview the markdown, it displays the ISO relationships for everyone in the team model. It outputs the roles they have in the ISMS, their position descriptions, responsibilities, and authorities. Since Matt is the CSO, he has multiple roles, so there is a detailed listing, including any ISO clauses assigned to him. These clauses have owners, such as MD being listed as an owner, and assets like policies, procedures, and other documents such as the CCTV policy.
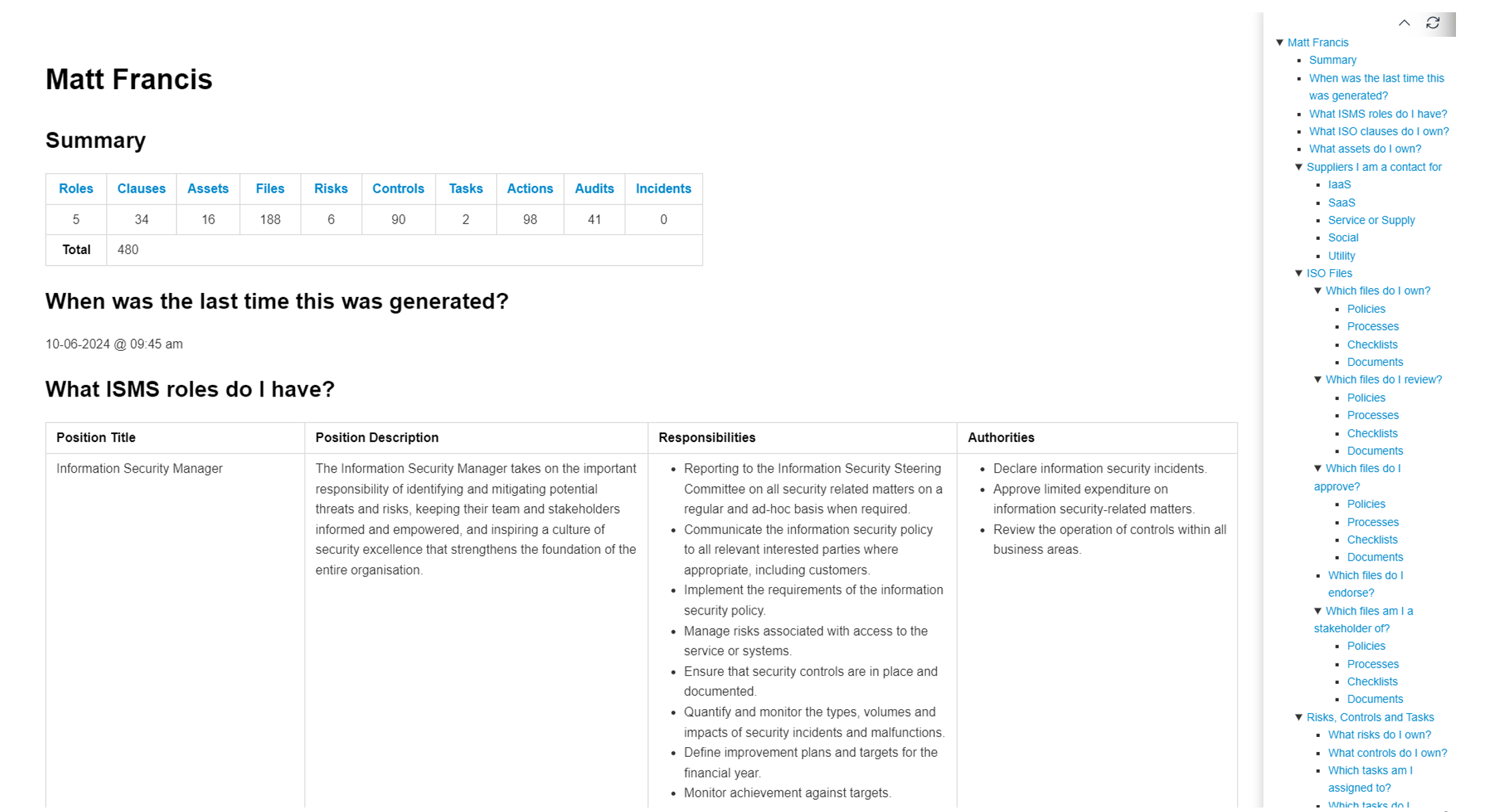
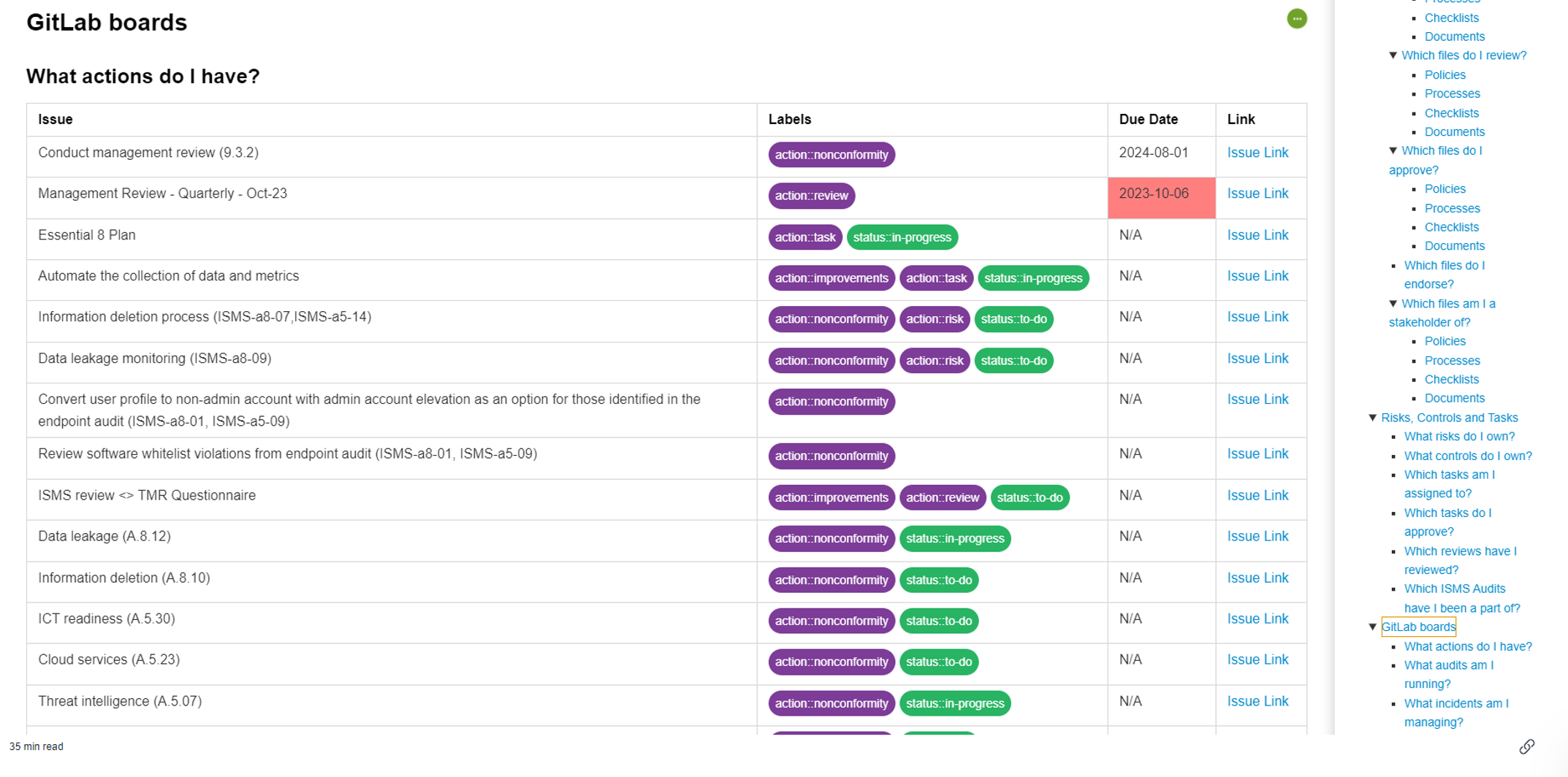
The preview also lists documents that Matt reviews and approves, controls he owns, and any risks or tasks assigned to him. This preview will also show on GitLab assignments, such as tasks on incident boards. For example, if Matt is assigned to a power outage task in Gitlab, it will appear on the cheat sheet. When checking out my own preview, it shows that nothing has been assigned to me, which makes sense since I’m a marketing team member. This feature allows anyone to verify and double-check assignments.
To achieve this, Nathan had to restructure their approach to include files, documents, reviewers, and teams through a more modular framework. Previously, all these elements were interconnected within a single model. Since the restructured approach, when referencing an individual in documents, for example, the system directly correlates them with their respective team. This required Nathan to update various templates to reflect these changes. For instance, the Risk register template used to refer to the original ISMS. Now, it points directly to specific registers, simplifying the extraction of all registered risks.
Conclusion
In conclusion, Nathan's work on updating WorkingMouse's ISMS metamodels and integrating an ISMS cheat sheet via Codebots and GitLab represents a significant enhancement in our information security management. This shift from centralised to modular meta models improves flexibility and efficiency, supporting current ISO27001 standards while preparing us for future ISMS adaptations. By streamlining roles, responsibilities, and document management, we enhance transparency and operational clarity across teams. This proactive approach highlights WorkingMouse’s commitment to maintaining strong information security practices and adapting to evolving cybersecurity landscapes. Find out more about our ISO27001 accreditation journey here!






